How to Install the Metasploit Framework
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.
Luckily for those of us who use Apple machines, the install process is much less time-consuming than it used to be. Just a couple of years ago, I would have had to download all the required pieces and configure them manually. Now, the Metasploit Framework has an install package for macOS (previously called Mac OS X).
Of course, we could use the Metasploit that's in our Kali Linux VM we just installed, but I generally only use Kali when a tool is unavailable for Macs, such as Aircrack-ng. Plus, running tools directly on your main operating system is generally faster and easier than running them in a virtual machine.
Step 1Download the Metasploit Framework Installer
Our fist step is to download the Metasploit installer package from Rapid7.
There are different editions, such as Pro, Express, Community, and Framework. Express costs $5,000, and Pro about 6 times that, and it's probably safe to say most of us don't have that kind of cash lying around. While the Community edition is free, we want the command-line interface, Metasploit Framework.
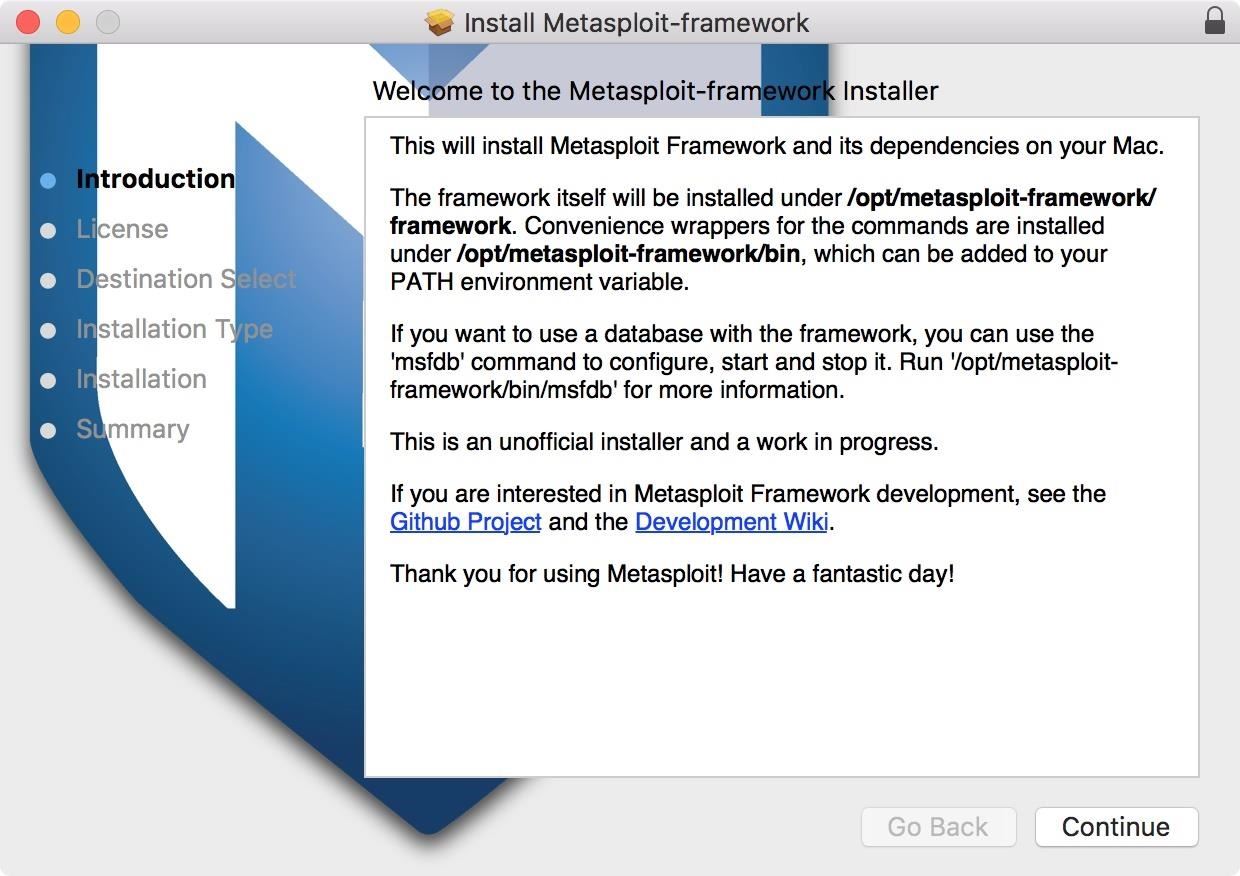
To save you some time, here is the download for Mac. Once it has downloaded, open the package and follow the directions in the installer. You will be prompted to enter your password.
Step 2Configure Metasploit
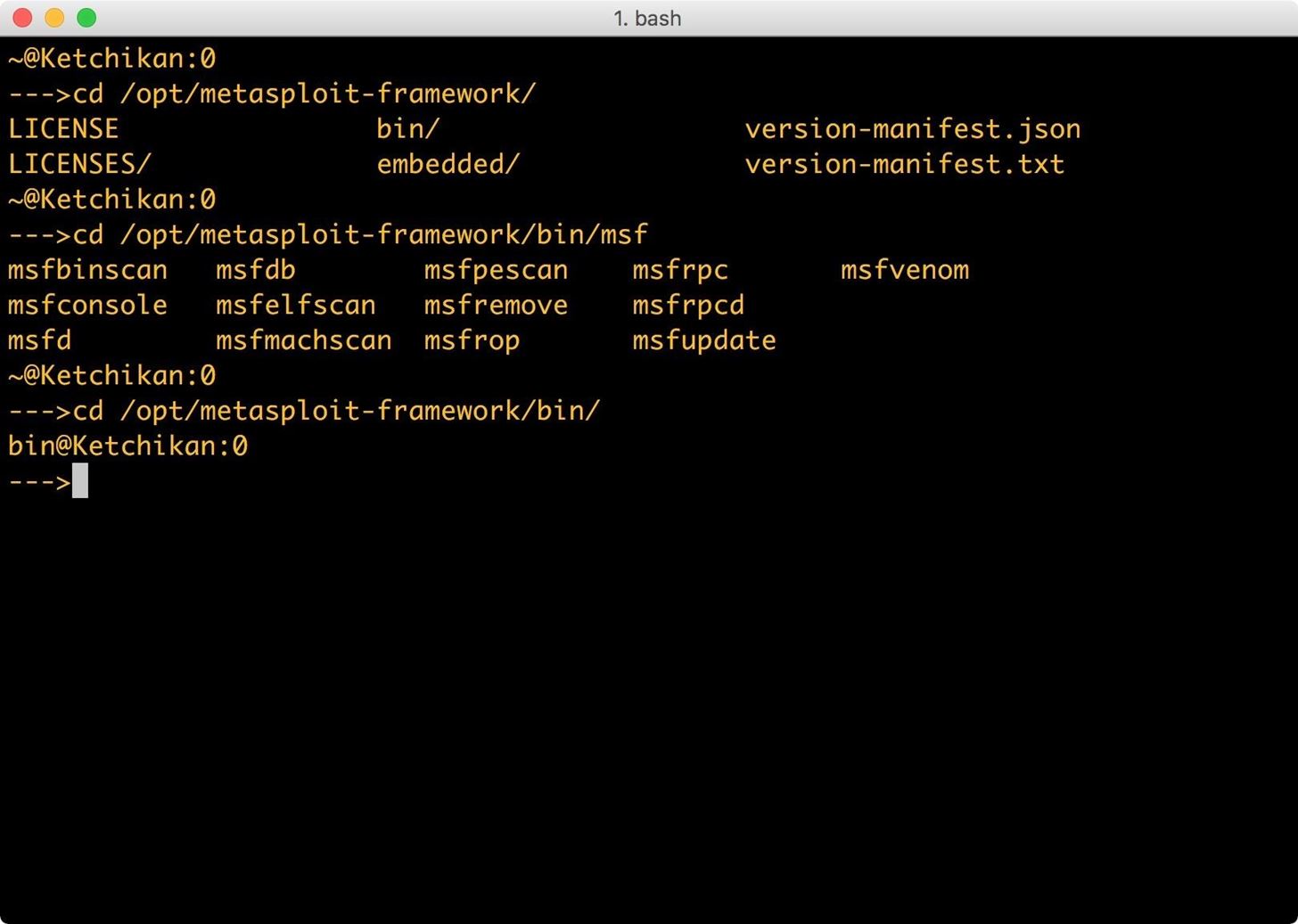
Now we will need to configure Metasploit. Open a terminal window and change directories to the folder containing msfconsole (the main interface for the Metasploit Framework):
- cd /opt/metasploit-framework/bin/
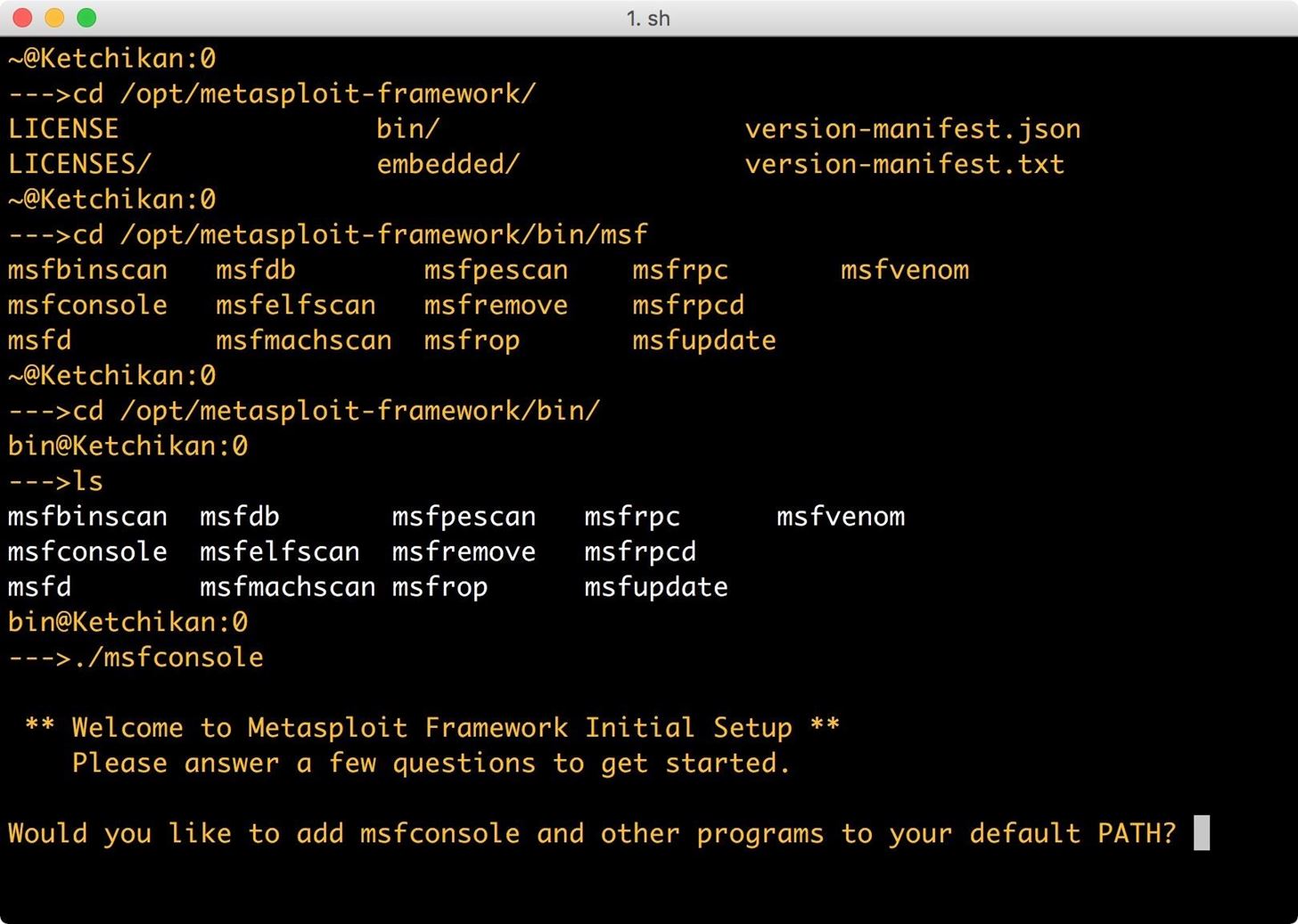
Next, run msfconsole with the command:
- ./msfconsole
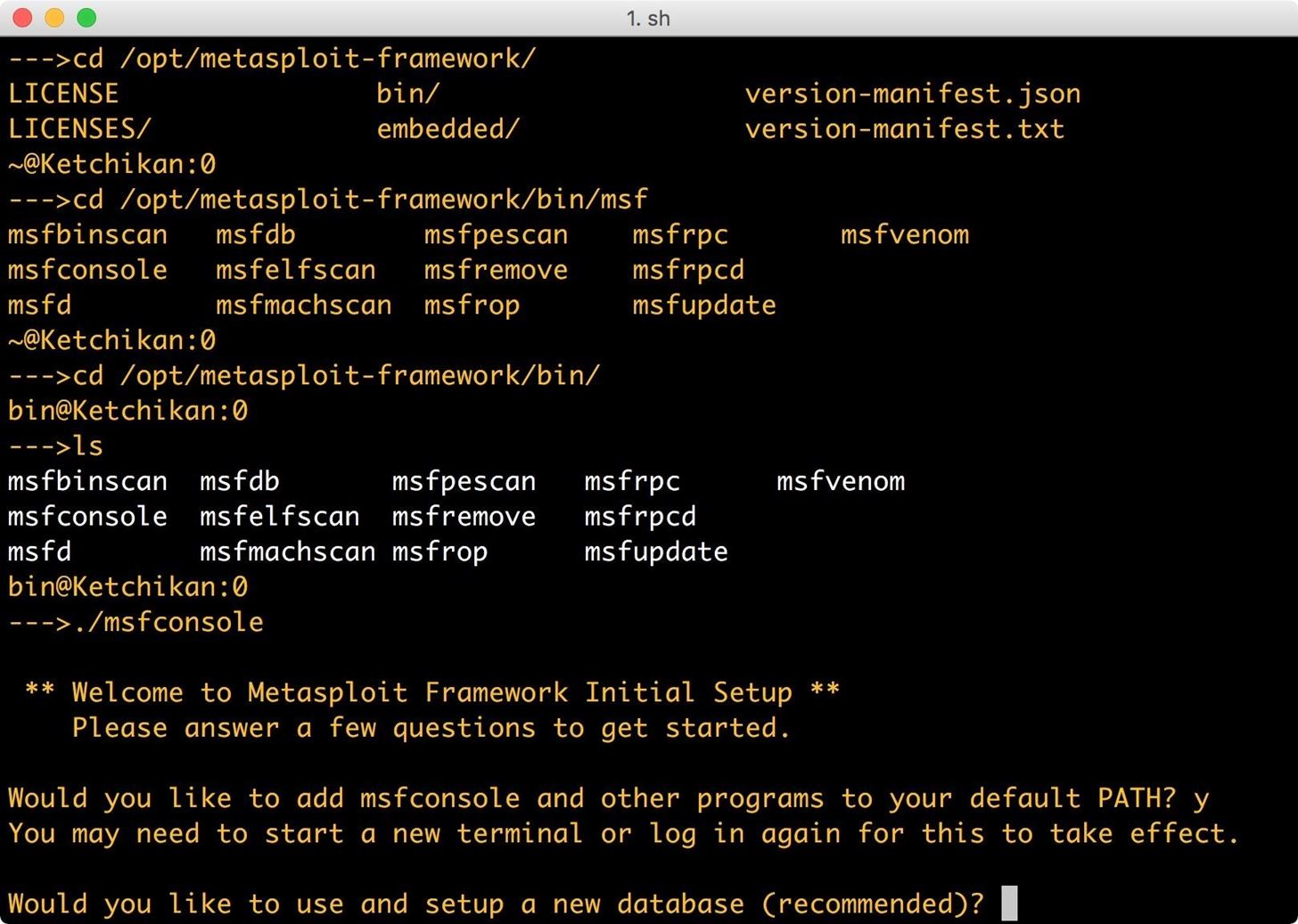
The first question asks if you want to add /opt/metasploit-framework/bin to your path. Select yes, so you can execute msf commands from any working directory.
Next, you will be asked if you want to set up a new database. Installing the database will allow us to list credentials, list hosts, and more—which is what we want.
Once the database is set up, msfconsole will drop you into the msfconsole! The install is complete.
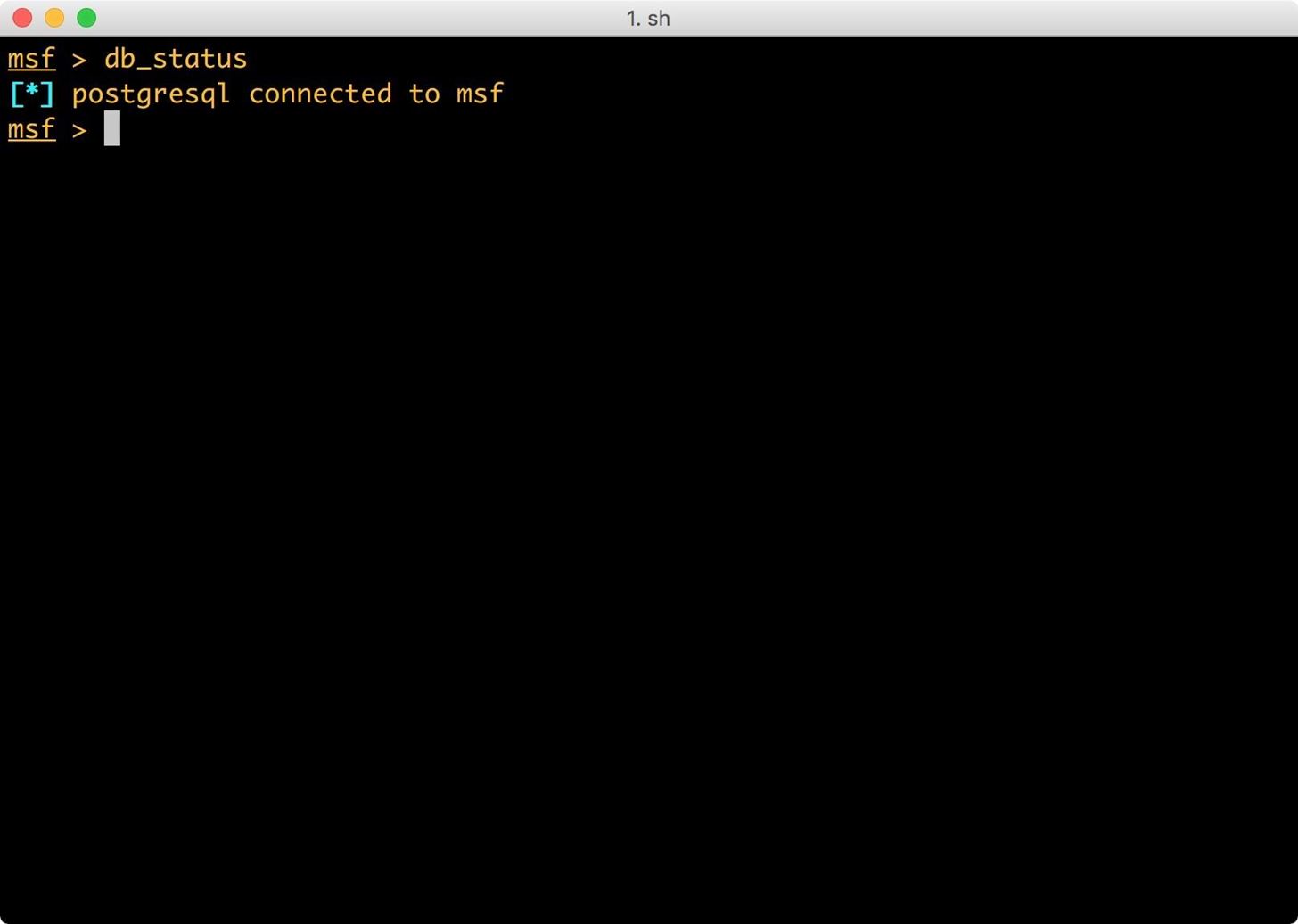
Now let's check to see if the database is working:
- db_status
As we can see, the database is connected and working.
Step 3Update Metasploit
Before diving into the basics of Metasploit, let's make sure it's up to date first. In a terminal window, execute the command:
- msfupdate
You will be prompted for your root password. Once given, Metasploit will update.
Now Get Hacking!
Installing Metasploit on macOS has never been easier. With Metasploit installed and running, you should be able to get hacking right away, so make sure to search here on Null Byte for some good guides that use msfconsole. We've got plenty to keep you occupied for a long time.
Installing many other hacking tools on macOS is also a cinch—the inclusion of Ruby and Python with the OS really help with this. But it's not only the languages, having a POSIX-compliant backend means that porting software from Linux to Mac is easier. Apple products seem to have become more popular with developers and IT professionals, and the more IT professionals using them, the more ports we'll see!
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar